Amethyst is an app built for the Android operating system, designed to facilitate interaction with the Nostr network. This platform offers a unique alternative to traditional social media by promoting direct, intermediary-free communication between users.
In this article, we’ll explore the features, technical aspects, and benefits of the Amethyst app, while also examining its importance in the growing landscape of decentralized social networks.
Let’s get started!
Table of Contents
What Is Nostr?
Nostr is a decentralized communication protocol built on public key cryptography. It supports the development of decentralized social network applications and peer-to-peer communication channels. The primary aim of Nostr is to enable information exchange without relying on central servers, prioritizing user privacy and freedom of expression.
Unlike traditional social media platforms, where companies control both the platform and message storage, Nostr gives users the freedom to choose their relays, granting full control over where their data is stored.
The Amethyst App for Android
Amethyst, developed by Vitor Pamplona, is a Nostr client designed specifically for Android devices. This open-source application has a vibrant community of over 100 developers actively contributing to its ongoing improvement.
Known for its user-friendly interface, Amethyst excels at delivering an intuitive user experience within a decentralized environment.
In the sections below, we’ll explore its key features and discover what sets it apart from other social media clients.
Ready to dive in? Let’s go!
Key Features of Amethyst
1. Intuitive User Interface
Amethyst is designed with simplicity in mind, offering a graphical interface similar to conventional social networks. However, it is backed by a robust technical infrastructure that ensures greater privacy and freedom for users.
The app focuses on delivering an effortless user experience, making it easy for even those unfamiliar with decentralized networks to navigate and interact seamlessly.
2. Profile Creation and Management
Amethyst uses a unique system where each user’s profile is identified by a public key, serving as their primary identifier on the Nostr network.
To maintain security, users safeguard a private key, which is used to sign messages and authenticate their profiles. This public-private key system eliminates the need for traditional account creation with email and passwords, enhancing security and anonymity for users.
3. Authenticated Messages
A core feature of Nostr is that all user messages are digitally signed, allowing any user on the network to verify their authenticity. This ensures the integrity and legitimacy of interactions across the platform.
Amethyst leverages this functionality to prevent message manipulation and create a trusted communication environment for its users.
4. Relay Connections
To communicate on the Nostr network, Amethyst allows users to connect to different relays. This flexibility is one of the most important aspects of Nostr, as it allows users to choose which servers they want to use to store and relay their messages.
Amethyst thus provides an easy-to-configure interface so that users can add and remove relays as needed, optimizing data distribution and increasing network resilience.
5. Security and Privacy
Amethyst, built on the Nostr protocol, ensures message privacy through end-to-end encryption.
The app does not collect user data, and all interactions occur directly between devices and network relays. By avoiding centralized servers and refraining from storing personal information, Amethyst significantly reduces the risk of data exposure to potential attackers.
A noteworthy addition to Amethyst is its support for the Tor network.
What is the Tor Network?
The Tor network (The Onion Router) is an anonymity system that uses multiple layers of encryption to protect data traffic. As data passes through a series of servers (called “nodes”), each layer of encryption is gradually removed, making it nearly impossible to trace the origin of the data. Tor is widely used to enhance privacy and protect users from identification or tracking online.
How Tor Enhances Amethyst
With Tor integration, Amethyst provides an additional layer of security and anonymity. This feature is particularly valuable for platforms prioritizing privacy and freedom of expression. By using Tor, Amethyst helps users maintain anonymity, prevent third-party censorship, and block attempts to monitor or filter network traffic. This ensures safer, more private communication for its users.
6. Bitcoin Integration
Amethyst integrates seamlessly with the Bitcoin network through the Lightning Network, enabling innovative payment features like the “value4value” model.
This model allows users to directly and financially support their favorite content creators, fostering a transparent and decentralised approach to monetization. With no hidden rules or risks of losing sponsorships due to adherence to arbitrary standards, this mechanism brings a revolutionary shift to the content creation landscape.
Architecture and Technologies Used in Amethyst
Amethyst is built with Kotlin, one of the most advanced programming languages for Android app development.
The app’s architecture follows the principles of the reactive programming model, enabling efficient communication and real-time updates for messages received from relays.
Use of Kotlin and Android Jetpack
As mentioned earlier, Amethyst is developed in Kotlin, a language known for its concise syntax and enhanced error safety compared to Java.
Additionally, the integration of Android Jetpack further enhances the app by enabling the use of modern, modular components, making it both scalable and easier to maintain.
Local Storage and Relay Synchronization
While Nostr primarily depends on relays for storage, Amethyst enhances user experience by utilizing local storage to cache messages. This not only improves loading speed but also enables users to access content offline.
Relay synchronization is handled automatically, ensuring the cache stays up-to-date while minimizing mobile data usage.
Using Amethyst in Practice
Now that you understand what Amethyst is, let’s dive into how to use it!
1. Creating an Account
To get started with Nostr, you’ll need to create a pair of keys:
- A private key
- A public key
When you first open the Amethyst app, you’ll be greeted with a screen to either access an existing account (by importing a key if you’re migrating from another Nostr client) or create a new one.
In this example, we’ll focus on creating a new account:
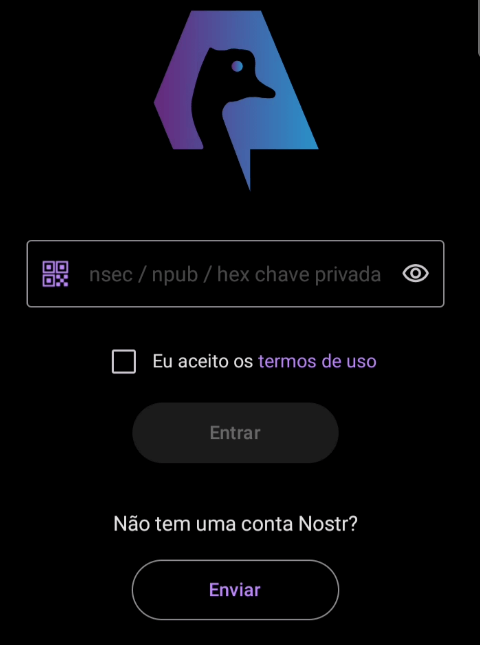
Under “Don’t have a Nostr account?”, click on the “Submit” button. You will then be redirected to the following screen.
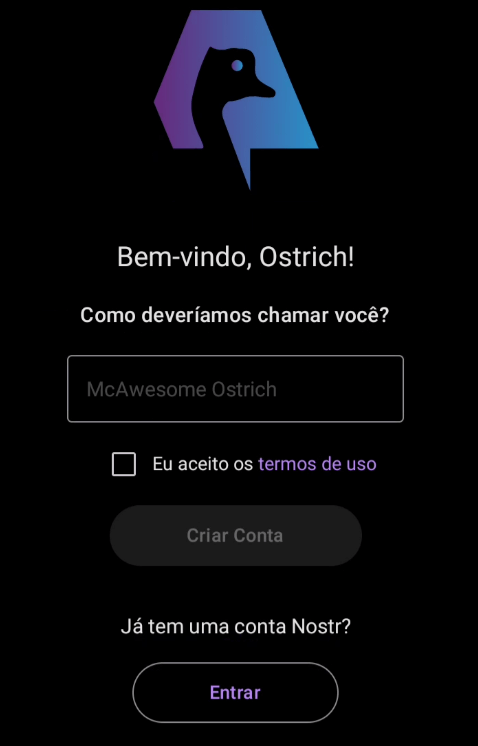
Choose a name for your username and click on “Create Account”.
By default, your “feed” (home page) will be empty.
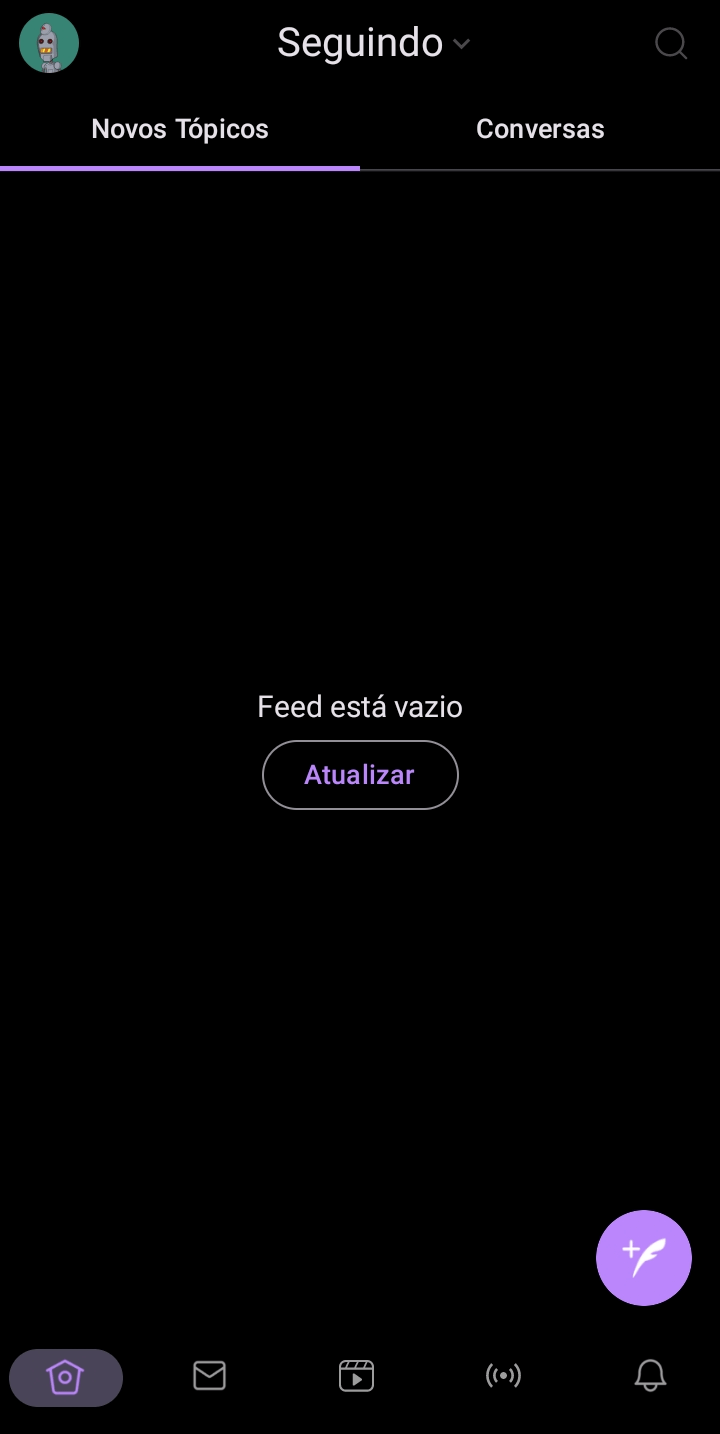
2. Searching for Other Users
From the main page, click on the magnifying glass icon (in the top right corner) and type in the name of the profile you are looking for.
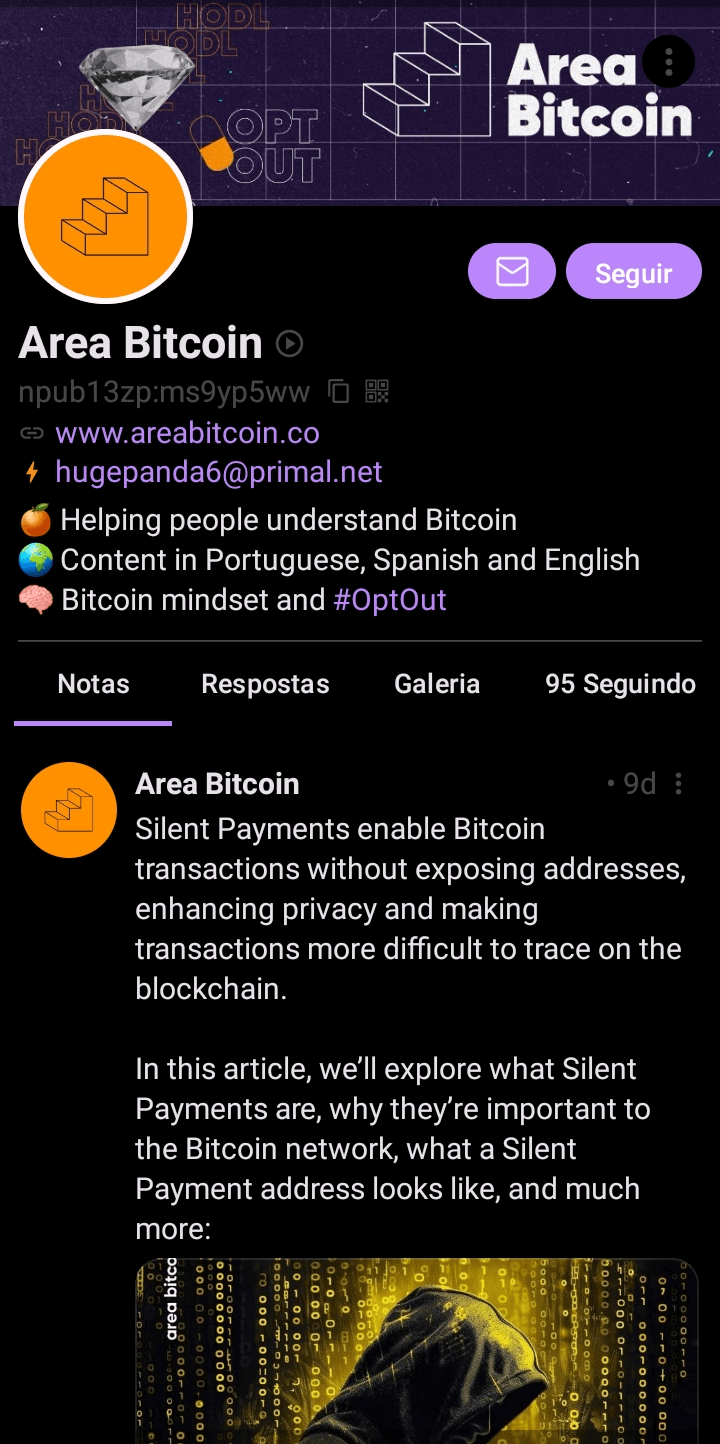
In this example, we will search for the Area Bitcoin profile.
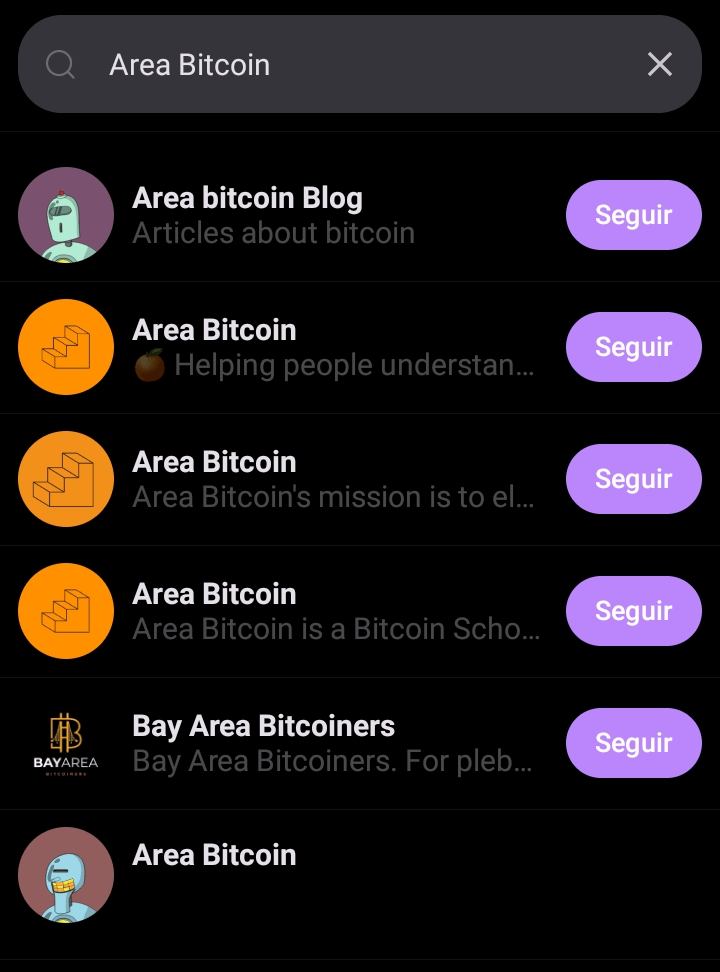
Be cautious of profiles attempting to impersonate the one you’re searching for, especially if it belongs to a public figure or a well-known institution.
To ensure you’re accessing the correct profile, use its public key, which is unique across the network.
Therefore, the Area Bitcoin public key is: npub13zpemj05wvgadhgyyv4e0captmkd64p8kz323pfq87ffahrws0ms9yp5ww
Follow us while you’re at it! 😉
3. Making a Post (Note)
In Amethyst, you can post notes publicly to everyone connected to the same relays as you or send private messages to specific users.
3.1 Sending a public note
From the home page, click on the pen icon (in the bottom right corner) and a screen containing a a text box will appear.
Once you have finished entering your text, click on “Save”.
3.2 Sending a private note
From the page of the profile you wish to chat with privately, click on the envelope icon at the top of the screen and a screen similar to the one shown below will appear.
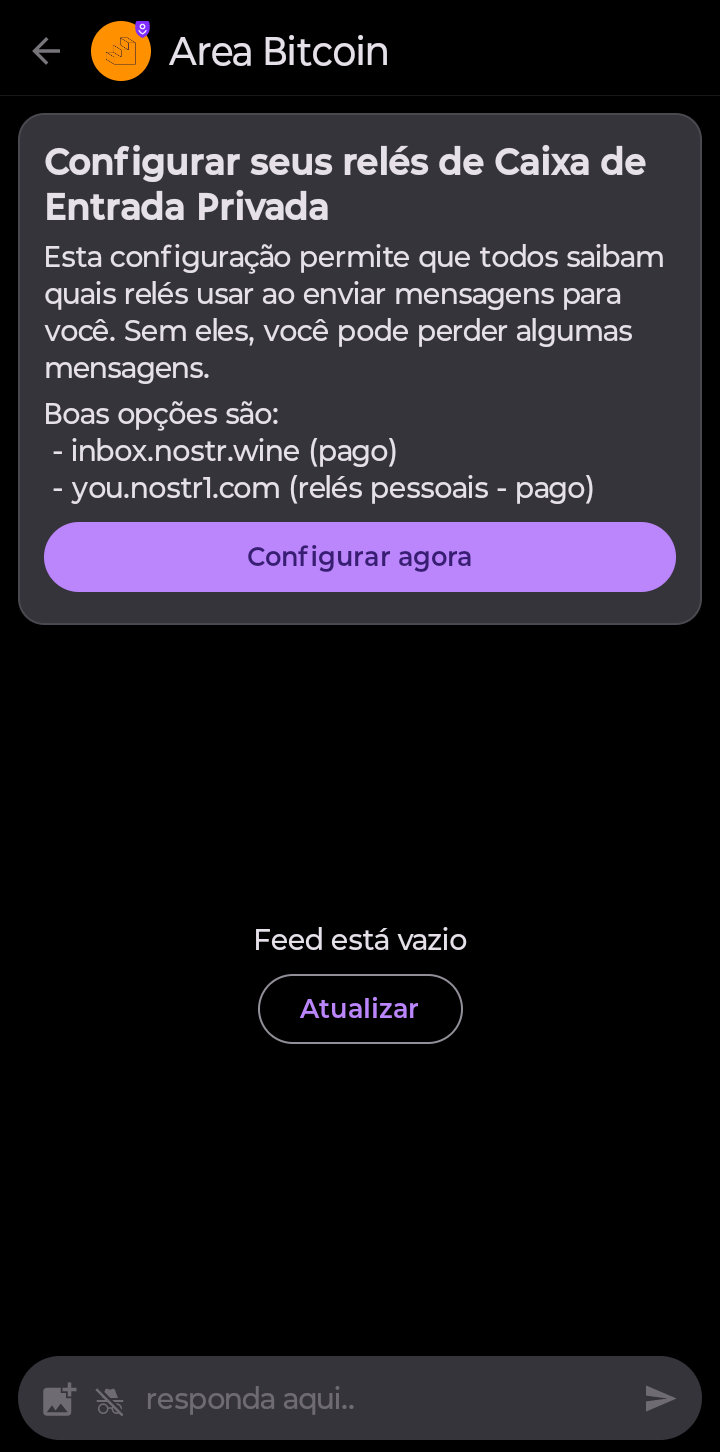
In the text box labeled “reply here…”, type the message you want to send. Once you’re finished, click the airplane icon to send it.
Back on the home page, you can view all the private messages you’ve sent by clicking the envelope icon located in the bottom bar of the app screen.
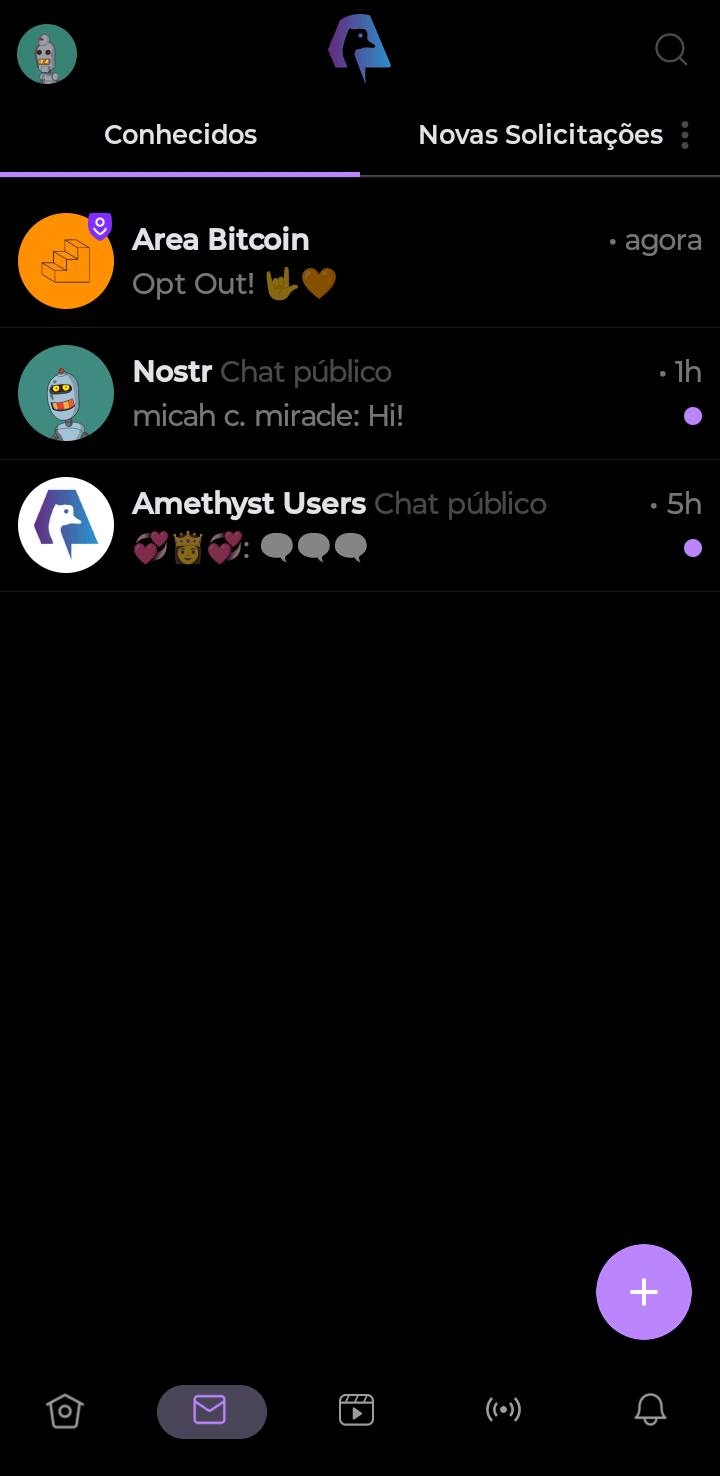
In addition to your sent messages, the app will display all messages from the Nostr global channel and the Amethyst channel.
If you’d prefer not to receive notifications from these channels, you can choose to “unfollow these channels.”
4. Connecting your Bitcoin Lightning wallet to Amethyst
While still on the main page, click on your profile picture to display the side menu.
Now, click on “Profile” and then click on the icon next to the envelope to edit your account information.
Click on the icon next to the envelope to edit your account information.
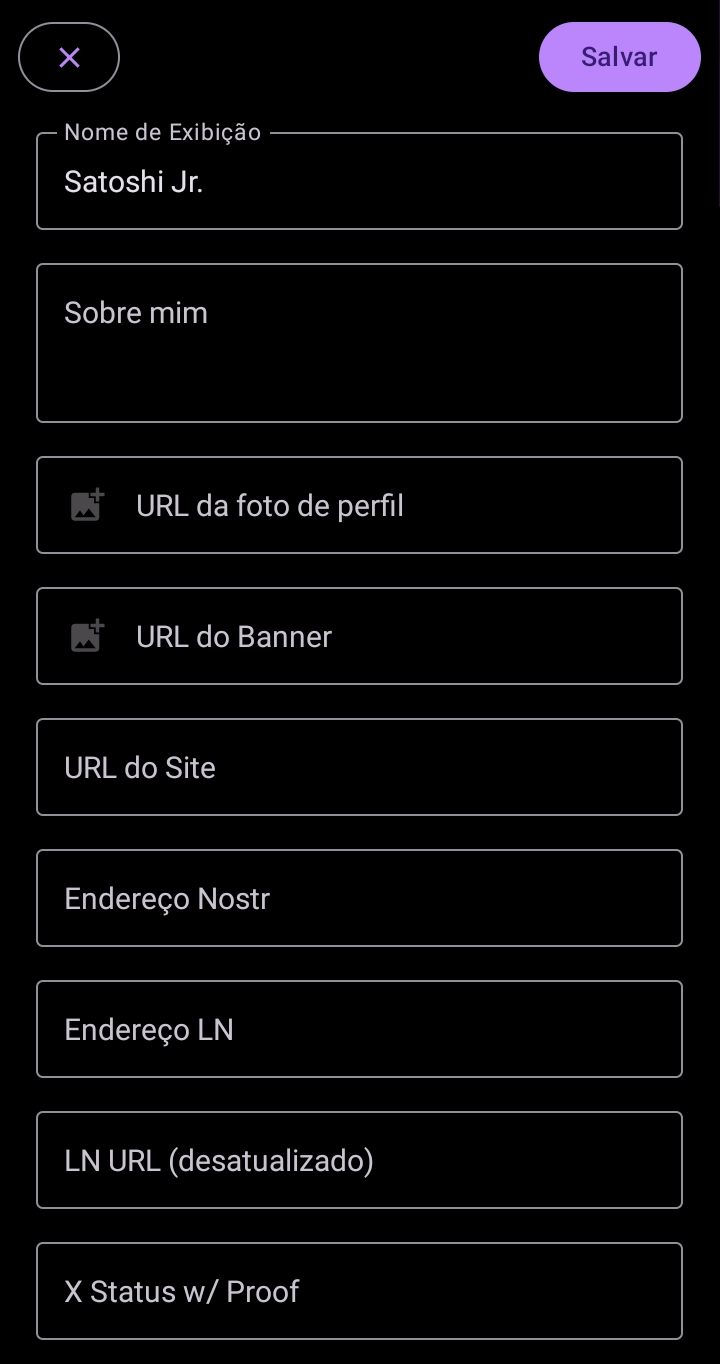
Once done, enter the address of your Lightning wallet in the “LN Address” region and then click on “Save”.
5. Structure of a note in Amethyst
Notes (posts) shared on the Nostr network and displayed in the Amethyst app follow a structured format, as shown in the screenshot below.
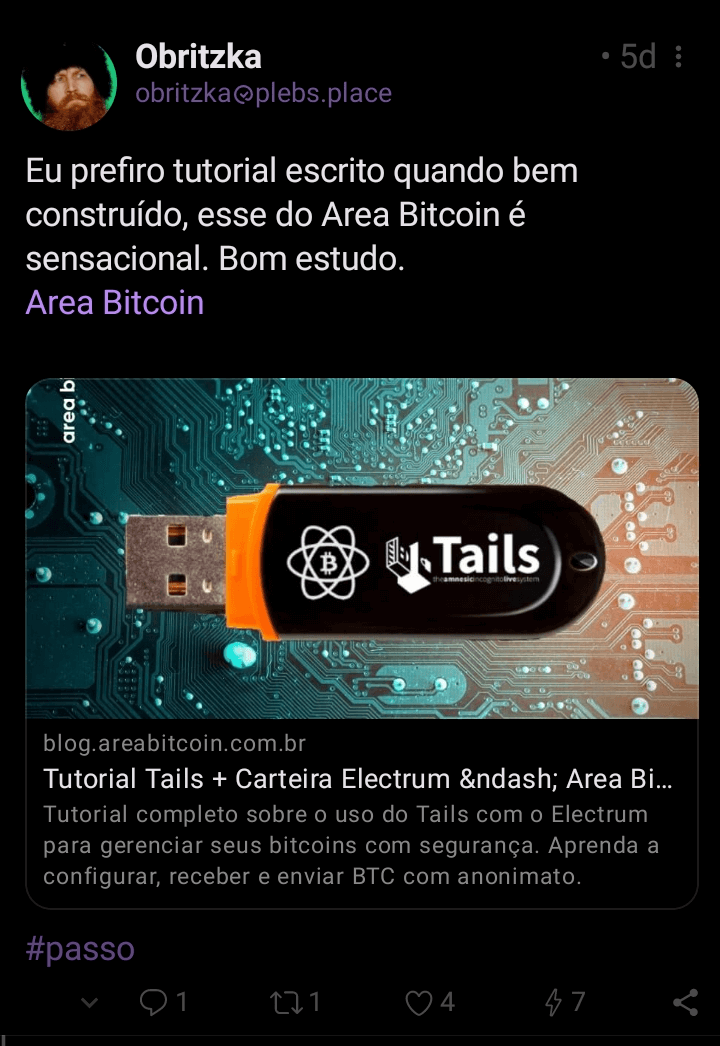
From left to right at the bottom of a note, you’ll see:
- The number of comments on the note.
- The number of reshares.
- The number of reactions, which can include any emoji.
- The number of zaps sent for that note.
By the way, zaps are satoshis (small Bitcoin units) sent to support a post. For example, in the note shown above, 7 satoshis were sent.
6. Sending a Zap
To send a Zap, ensure your Lightning wallet is connected to your account. Select a publication you want to support with Zaps. For this example, we’ll choose a publication from one of Nostr’s creators, fiatjaf. Simply click on the Lightning icon and select the amount you wish to send.
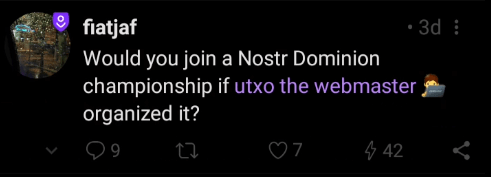
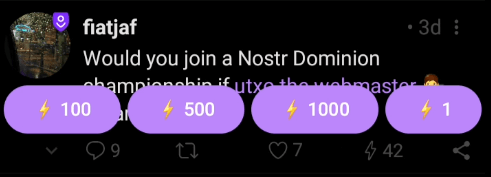
If you’d like to edit the pre-selected values, you can also customise which options will appear. Press and hold the Lightning icon until a new window opens. After making your changes, click “Save” to confirm.
Once you have finished making your changes, click “Save”.
7. Enabling TOR by default in your connections
Amethyst now includes built-in support for the Tor network, offering enhanced privacy features. You can choose to connect through software running a Tor proxy, such as Orbot, or let the Amethyst application handle the proxy setup directly.
To enable this, navigate to the side menu and click on “Privacy Options”. Adjust the parameters to suit your preferences or select one of the pre-configured profiles under “Tor Presets/Privacy”.
For example, selecting the “Full Privacy” option activates all available privacy features. Once you’ve made your adjustments, simply click “Save” to apply the changes.
8. Configuring connections with Relays
From the side menu, click on “Relays”. On the next screen, you can easily add or remove the relays you want to connect to, tailoring the setup to your preferences.
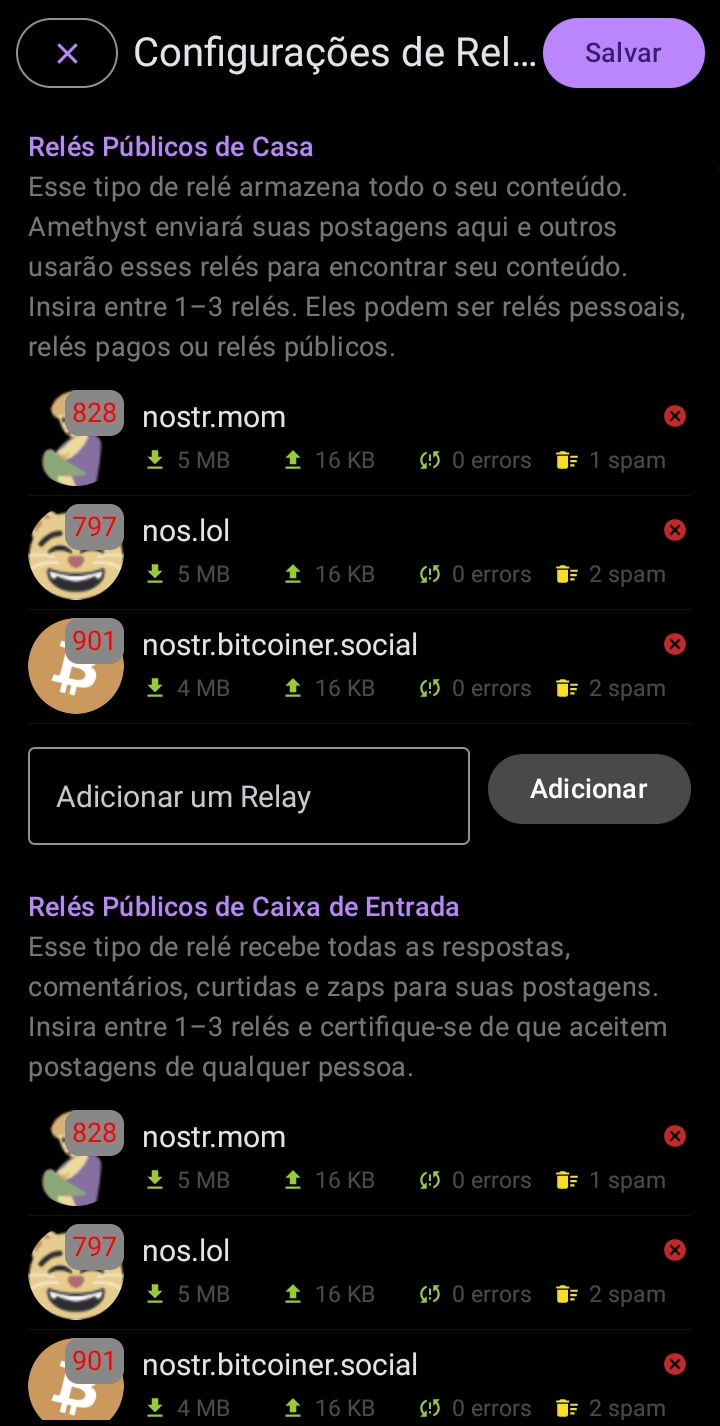
Now let me know, isn’t it easy?!
Benefits of Using Amethyst and the Nostr Network
1. Privacy and Data Control
One of the greatest benefits of Amethyst is the control it provides over personal data.
Unlike traditional social networks, where user data is stored on centralized servers, Nostr distributes data across relays.
With Amethyst, users can choose which relays to use, increasing privacy and giving them greater control over where their information is stored.
2. Freedom of Expression and Reduced Censorship
Nostr’s decentralization makes content censorship extremely difficult, as there is no centralized server to control or regulate.
Amethyst users have the freedom to express their opinions and share information without fear of being blocked or censored. This attracts many advocates of freedom of expression and network neutrality.
3. Scalability and Fault Tolerance
The relay-based architecture model allows Nostr to be scalable and fault-tolerant. Even if one relay goes offline, users can connect to other relays and continue accessing the network. Amethyst facilitates this switching, ensuring a more stable and reliable experience in decentralized environments.
4. Advanced Encryption and Security Support
Nostr’s public key encryption protects message content and ensures that only the legitimate sender can sign and authenticate messages sent.
Amethyst leverages this security infrastructure transparently, providing users with a platform where they can communicate securely without fear of their messages being intercepted.
Comparison with Other Nostr Clients and Traditional Social Networks
When compared to other Nostr clients like Primal or Damus, Amethyst offers a solid experience but has some usability quirks.
For instance, configuring default Zap values is less intuitive in Amethyst. Instead of having a dedicated section in the sidebar, users must hold down the Zap button for the configuration option to appear.
Another area where Amethyst falls short compared to Damus is in handling private key generation and confirmation.
When creating an account, Damus emphasizes securely storing the private key, displaying a screen for users to confirm they have recorded the key on paper or another secure method before accessing the network. This process closely resembles how Bitcoin wallets generate user seeds.
In contrast, Amethyst creates the account directly, requiring users to access their profiles afterward to securely store their keys.
However, Amethyst represents a substantial improvement compared to traditional social networks. It provides users with greater control over their data and employs an architecture that fosters freedom of expression.
Unlike centralized platforms like Facebook or X (formerly Twitter), Amethyst, in combination with Nostr, removes intermediaries, reduces censorship, and enhances security. This structural difference has a profound effect on privacy, as Nostr lacks a single control point or entity capable of selling, manipulating, or exploiting users’ personal data.
Challenges and Limitations of Amethyst and Nostr
Despite their many advantages, Amethyst and Nostr face several challenges:
- Learning Curve: For users unfamiliar with decentralized networks and encryption, navigating Nostr can present a steep learning curve, especially when accessing advanced features. While Amethyst offers a user-friendly interface, beginners may still struggle with concepts like public keys, relay configurations, and using the Tor network.
- Dependence on Available Relays: The quality of the Amethyst experience relies heavily on the availability and reliability of relays. If many relays go offline or implement fees to cover operational costs, this could disrupt communication and message storage within the network.
- “Lack” of Recommendation Algorithms: Amethyst and the Nostr protocol prioritize user control over data, intentionally omitting features like content recommendation algorithms and engagement analytics found in centralized platforms. For users accustomed to a “TikTok-style” experience, where content is algorithmically tailored to keep attention, Amethyst may feel “too manual” or monotonous, requiring a shift in expectations and mindset.
Final Thoughts
Amethyst marks a significant innovation in decentralized social networks, providing a platform where users have full control over their data and can communicate securely and privately.
With its user-friendly interface and robust security features, Amethyst enables users to fully harness the potential of Nostr, delivering an accessible and efficient experience.
Although it faces some technical and usability challenges, Amethyst represents a meaningful step toward freer and more secure online communication, where users retain ownership of their data.
In a time when privacy, censorship, and data control are at the forefront of conversations about the internet’s future, Amethyst and the Nostr protocol have the potential to redefine online interactions.
That’s all for now! I hope you found this article insightful. If you’re curious and want to explore Amethyst, give it a try and connect with us there.
Until next time, opt out!
Share on your social networks:
Area Bitcoin is an educational Bitcoin school that aims to accelerate the financial and intellectual sovereignty of all individuals.
Did you like this article? Consider buying us a cup of coffee so that we can keep writing new content! ☕